This post has been updated in 2020 to reflect the latest industry statistics on cyber attacks
Cyber attacks are on the rise and, according to cybersecurity expert Andy Swenson, small to mid-sized organizations are huge targets. And, during a worldwide crisis like the one we’re facing now with COVID-19, companies may be letting their guard down as they tackle the ripple effects of the pandemic – making them even more susceptible to hackers.
Swenson is the CEO of Tampa-based consulting company Delbridge Group, which provides digital security and IT consulting services for organizations across the globe. He recently shared with us the latest statistics around data breaches, the new types of attacks targeting users, and the steps businesses can take to protect themselves.
You may think your company is too small to be the target of a cyber attacker, but the reality is everyone is vulnerable. In 2013 and 2014, respectively, Target and Home Depot were victims of two of the biggest data breaches in U.S. history. While these giant retailers were the ultimate targets, their breaches were actually predicated by an attack on a small vendor that managed their heating and air conditioning systems. After hacking into the vendor’s system, attackers were able to tap into the retail organizations to steal millions of customers’ personal data, including credit card numbers.
“When it comes down to security, it really tends to be industry-agnostic because everybody’s a target,” says Swenson. “I counsel people to take as many steps as they can to protect themselves. Security measures should be treated like layers of an onion; as they peel back one layer, there’s another layer, and yet another layer. Every one of those layers will provide an opportunity to identify and thwart potential breaches.”
Since 2007, Verizon has published an annual data breach investigations report detailing the growing problem of cyber attacks. In 2019, there were more than 41,000 data security incidents and 2,013 confirmed data breaches worldwide. And, while these numbers are alarming, Swenson says they don’t include potentially thousands more incidents that were never reported. “If somebody gets taken for $10,000 because of an e-mail compromise or ransomware attack, they may not bother reporting it to law enforcement or their insurance company because they probably aren’t covered for such an event. These unreported attacks make it challenging to see the full magnitude of the problem.”
Verizon’s 2019 report found that 69% of the breaches were perpetrated by people outside of the victim’s organization, while 34% involved internal actors such as employees. And, of all the data breach victims, 43% were small businesses. Real threats are out there for small and mid-sized companies, which is why organizations must be more vigilant with their digital security measures.
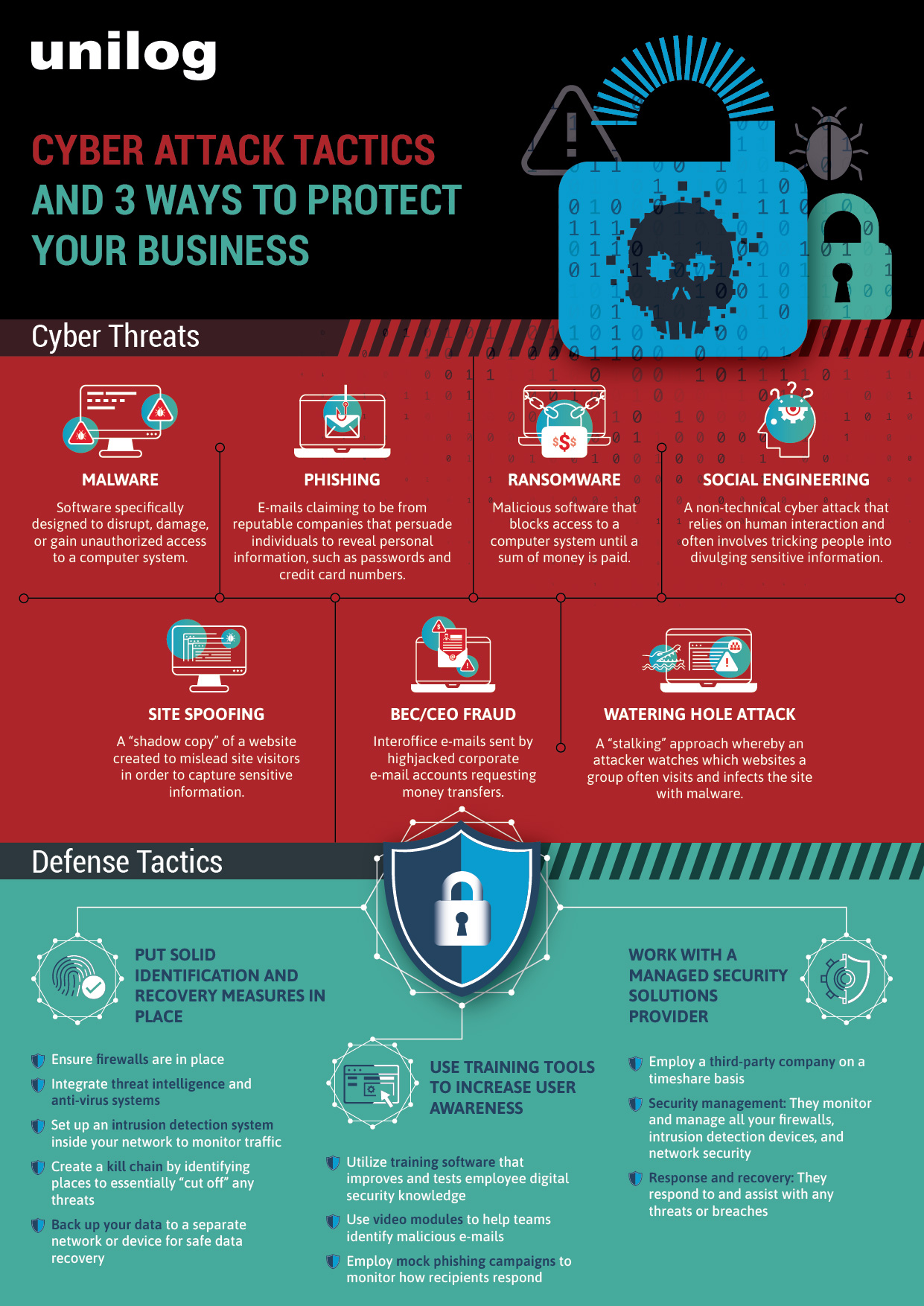
Cybercrime’s latest tactics
Digital attackers have become more sophisticated in their efforts to steal data, corrupt a system, or swindle a victim. Attackers target end users by tricking unsuspecting people via e-mail communications and websites. In fact, in 2019, 94% of malware attacks originated from an e-mail that contained a link. However, it is possible for malware to install directly from an e-mail without clicking a link. Once the e-mail is opened, additional malware is downloaded and installed directly onto the user’s device.
Another tactic, known as a watering hole attack, is directed toward a particular group of users. The attacker watches which websites a group often visits and infects the site with malware. Eventually, a member of the group becomes infected by the malware, allowing the attacker to gain access to the user’s place of employment. Swenson says the watering hole attack was originally directed at large technology companies like Apple and Microsoft, where attackers embedded malware into the discussion boards and chat sites used by their software engineers. Unbeknownst to the engineers, they picked up some of the malware on their laptops, which then compromised their organizations.
A cyber tactic that is particularly prevalent with small businesses right now is called business e-mail compromise (BEC) or CEO fraud. Here, the attacker gains access to a corporate e-mail account, spoofs the owner’s identity, and sends out interoffice e-mails requesting money transfers. For example, they’ll send an e-mail that looks as though it’s from the CEO or CFO of a company to someone in the finance department, requesting they transfer money to an account. The finance employee doesn’t question the e-mail, seeing as it’s from one of their executives.
“The better attackers will do an awful lot of groundwork with this scheme. They’ll break into an organization’s system, research a person’s e-mail connections, and determine who will most likely fall for their phony transfer request,” explains Swenson. “These attackers actually get people to transfer significant amounts of money. Unfortunately, that money is long gone by the time anyone figures it out.”
Swenson suggests playing it safe when it comes to e-mails requesting money. Start by establishing normal protocol behavior and make sure everyone within your organization understands the process to request and approve money transfers. Then, if you do receive an e-mail requesting money, verify it. “Pick up the phone and call the person asking for the money, or walk down the hall to ask them in person. Take the time to make sure it’s a legitimate request,” adds Swenson.
Mobile vulnerabilities
In Verizon’s latest report, they warned against the high susceptibility of social engineered attacks on mobile devices as a result of their design and the way people interact with their phones. With smaller screen sizes and lack of easy page navigation, mobile devices make it harder for users to closely review e-mails, links, and requests. In addition, mobile OS and apps don’t allow verification of website pages or e-mails, so users aren’t notified of suspicious or fraudulent items viewed on their devices. But as Verizon pointed out, the bigger vulnerability issue could be the user himself. As more people multi-task while on their devices, they’re not paying attention to incoming information that could create a security breach, which is why mobile users must be more vigilant in detecting e-mail-based phishing, spoofs of legitimate web pages, and social engineering attacks via social media platforms.
Protect yourself and your organization
Small and mid-sized organizations may find it challenging to create and maintain a secure environment when they have limited resources, which is why some companies rely solely on firewalls as their first and last line of defense. Swenson maintains that, while firewalls are necessary as a security measure, they alone will not solve all your problems. He offers three steps your organization can take to further protect yourself:
- Put solid identification and recovery measures in place
In addition to firewalls, integrate threat intelligence and anti-virus systems to help identify threats. Swenson also suggests setting up an intrusion detection system inside your network to watch and monitor traffic. This intuitive detection system learns the behavior of the users, identifies atypical or abnormal activities, and triggers an alert of any red-flagged actions.
Next, create a kill chain by identifying places to essentially “cut off” any threats before they do any damage. It starts by identifying and not opening phishing e-mails. If you make the mistake of clicking on an e-mail or a link to a bad website, put in a defense measure to block access to it. At the point that the malware comes in, identify that it’s malware and block it from running on your computer. If the incident gets past that point, you still have an opportunity to stop any data from going out of your network. The more places you have linked in your kill chain, the better change you’ll have of beating the attackers.
Finally, have a proper recovery measure in place. With ransom/cryptoware, the first thing attackers attempt to do is destroy your backups. Be proactive and back up your data regularly but, more importantly, back up your data to a separate network or device that is not attached to your main network. By having your backup data stored offline, attackers can’t access it to encrypt it.
- Use training tools to increase user awareness
There are a number of educational tools and training available to make employees more aware of the digital security threats out there, and teach safe, best practices. Swenson suggests taking advantage of affordable tools such as Proofpoint, PhishMe, and KnowBe4 to improve employee digital security knowledge. Through the help of video vignettes and training modules, users can be taught how to identify malicious e-mails, and then tested to reinforce their learning. Many of these tools include phishing campaign software that allows a company to send out mock phishing e-mails throughout their organization to monitor how recipients respond, effectively testing their employees and teaching them the difference between good and bad correspondence.
- Work with a managed security solutions provider
Having an in-house IT security department is not an option for many small businesses. However, companies can hire a third-party security solutions provider that gives them all the benefits and resources of a fully staffed security group, but on a timeshare basis. These digital security companies share their services across other businesses to provide a cost-effective option for smaller organizations. For a monthly fee, their security operations center will monitor and manage all your firewalls, intrusion detection devices, and your network security. They’ll also receive copies of all the information that is collected from those systems and take action, just like a help desk, to assist with anything that looks like it could be a security incident. “Depending on the size and scope of your network, it may cost a couple thousand dollars a month to have professionals manage your entire network environment to ensure it’s secure,” says Swenson. “That’s a small investment considering, if something actually happens in your organization, they can help walk you through the recovery process. That’s crucial.”
The end goal is to put yourself in a position where you don’t have to worry about your digital security. With the help of technology, training tools, and digital security professionals, your employees and your organization can be proactive and vigilant in staving off cyber attackers.
For more solutions from cybersecurity consultant Andy Swenson, connect with him on LinkedIn or visit delbridgegroup.com.